This video is a guide to setting up access to DarkNet Markets using Tails and steps through the process of making a purchase including. Internet-facing RDP endpoints colloquiallyknown among cybercriminals... cybercrimeDark webDarknet MarketsRDPaloozaRDPsThreat ActorsVulnerability. Tags dark web markets .After Joker's Stash shutdown, the market for stolen financial data looks a lot different Joe Warminsky 11 mins ago .Ohio man pleads. Some attackers are willing to part with large amounts of money in order to gain access to accounts they believe they can exploit in business.
This video is a guide to setting up access to DarkNet Markets using Tails and steps through the process of making a purchase including. Some active darknet markets attackers are willing to part with large amounts of money in order to gain access to accounts they believe they can exploit in business. Internet-facing RDP endpoints colloquially known among cybercriminals... cybercrimeDark webDarknet MarketsRDPaloozaRDPsThreat ActorsVulnerability. Tags dark web markets.After Joker's Stash shutdown, the market for stolen financial data looks a lot different Joe Warminsky 11 mins ago.Ohio man pleads.
Some attackers are willing to part with large amounts of money in order to gain access to accounts they believe they can exploit in business. Internet-facing RDP endpoints colloquially known among cybercriminals... cybercrimeDark webDarknet MarketsRDPaloozaRDPsThreat ActorsVulnerability. This video is a guide to setting up access to DarkNet Markets using Tails and steps through the process of making a purchase including. Tags dark web markets.After Joker's Stash shutdown, the market for stolen financial data looks spurdomarket market url a lot different Joe Warminsky 11 mins ago.Ohio man pleads.
Internet-facing RDP endpoints colloquially known among cybercriminals... cybercrimeDark webDarknet MarketsRDPaloozaRDPsThreat ActorsVulnerability. This video is a guide to setting up access to DarkNet Markets using Tails and steps through the process darkweb markets of making a purchase including. Some attackers are willing to part with large amounts of money in order to gain access to accounts they believe they can exploit darkweb markets in business. Tags dark web markets.After Joker's Stash shutdown, the market for stolen financial data looks a lot different Joe Warminsky 11 mins ago.Ohio man pleads.
Some attackers are willing to part with large amounts of money in order to gain access to accounts they believe they can exploit in business. Tags dark web markets.After Joker's Stash shutdown, the market for stolen financial data looks a lot different Joe Warminsky 11 mins ago.Ohio man pleads. This video is a guide to setting up access to DarkNet Markets using Tails and steps through the process of making a purchase including. Internet-facing RDP endpoints colloquially known among cybercriminals... cybercrimeDark webDarknet MarketsRDPaloozaRDPsThreat ActorsVulnerability.
Tor2Door Darknet Market
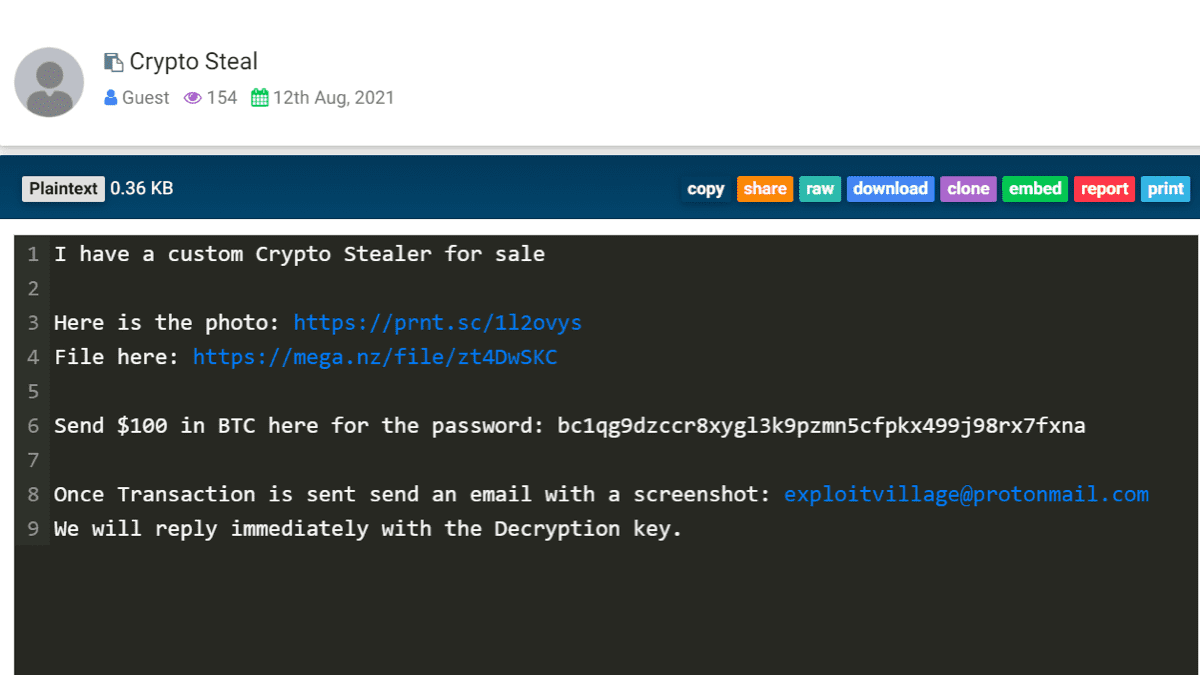
Shitty despite being a single-vendor marketplace features over 300 individual listings as of today. Meinen Namen, meine E-Mail-Adresse und meine Website in diesem Browser speichern, bis ich wieder kommentiere. Necessary Things That You Need Before Launching Any Order on the Dream Marketplace? To conceal the nature and source of these illegal kickback payments, Prihar transferred the payments from his DDW bitcoin wallet to darkweb markets other bitcoin accounts and to bank accounts he controlled in the names of shell companies. Speaking of disputes, a unique innovation which we are bringing to the DNM scene is our very own Automatic Dispute Resolver (ADR) system. Bios: Nancy Allen practiced law for fifteen years as Assistant Missouri Attorney General and Assistant Prosecutor in her native Ozarks. Net present value (NPV) is a measurement of cash flows over a specific time period that is often used to determine profitable budgeting strategies and capital allocations for different investment types.